Round Key Generation In Aes Example
This is an exercise in secure symmetric-key encryption, implemented in purePython (only built-in libraries used), expanded from Bo Zhu's (http://about.bozhu.me)AES-128 implementation at https://github.com/bozhu/AES-Python
- AES-128, AES-192 and AES-256 implementations in pure python (very slow, butworks).Results have been tested against the NIST standard (http://csrc.nist.gov/publications/fips/fips197/fips-197.pdf)
- CBC mode for AES with PKCS#7 padding (now also PCBC, CFB, OFB and CTR thanks to @righthandabacus!)
encryptanddecryptfunctions for protecting arbitrary data with apassword
Nov 20, 2018 AES – Advanced Encryption Standard - Structure, Encryption Process, Round Key Size Relation - Hindi #AES Lecture in Hindi Computer Network Security(CNS) Lectures – Internet Security. ROUND KEY GENERATION FOR AES RIJNDAEL BLOCK CIPHER. The present invention relates to methods and apparatus for implementation of the Advanced Encryption Standard (AES) algorithm and in particular to methods and apparatus for real-time generation of the round keys required during the encryption and decryption rounds of the algorithm.
AES is a symmetric key encryption cipher, and it is generally regarded as the “gold standard” for encrypting data. AES is NIST-certified and is used by the US government for protecting “secure” data, which has led to a more general adoption of AES as the standard symmetric key. Jun 26, 2016 An explanation of the Key Generation or Key Expansion process in AES Algorithm. An explanation of the Key Generation or Key Expansion process in AES Algorithm. Skip navigation Sign in. The DFA attack on the AES-128 algorithm returning the last round key. For example, the DFA 5, an attack with faults injected on round 8, allows finding the round key K10 of AES-128. The same kind of fault respectivelly applied on round 10 and 12 of AES-192 and AES-256 during extension phase returns the last round key K12 and K14. Then the fault.
Note: this implementation is not resistant to side channel attacks.
Although this is an exercise, the encrypt and decrypt functions shouldprovide reasonable security to encrypted messages. It ensures the data iskept secret (using AES), blocks are encrypted together (CBC), the samemessage encrypted twice will have different ciphertexts (salt), the ciphertexthasn't been tampered with (HMAC) and the key has some defense against brute-force(PBKDF2).
The algorithm is as follows:
16 random bytes of salt are extracted from the system's secure random numbergenerator (usually /dev/urandom)>
The given master key is stretched and expanded by PKBDF2-HMAC(SHA256) usingthe salt from 1), to generate the AES key, HMAC key and IV (initializationvector for CBC).
The given message is encrypted with AES-128 using the AES key and IV fromstep 2), in CBC mode and PKCS#7 padding.
A HMAC-SHA256 is generated from the concatenation of the salt from 1) andthe ciphertext from 3).
The final ciphertext is HMAC + salt + ciphertext.
Security overview:
The random salt ensures the same message will map to different ciphertexts.
The HMAC ensures the integrity of both the entire ciphertext and the PKBDF2salt; encrypt-then-mac prevents attacks like Padding Oracle.
Bytes from keys, iv and salt are not reused in different algorithms.
PBKDF2 key stretching allows for relatively weak passwords to be used as AESkeys and be moderately resistant to brute-force, but sacrificing performance.
∟Introduction to DES Algorithm
∟DES Key Schedule (Round Keys Generation) Algorithm
This section describes DES (Data Encryption Standard) algorithm - A 16-round Feistel cipher with block size of 64 bits.
Key schedule algorithm:
DES key schedule supporting tables:
Permuted Choice 1 - PC1:
Permuted Choice 2 - PC2:
Left shifts (number of bits to rotate) - r1, r2, .., r16:
Table of Contents
About This Book
Round Key Generation In Aes Example Word
Cryptography Terminology
Cryptography Basic Concepts
Round Key Generation In Aes Example 2016
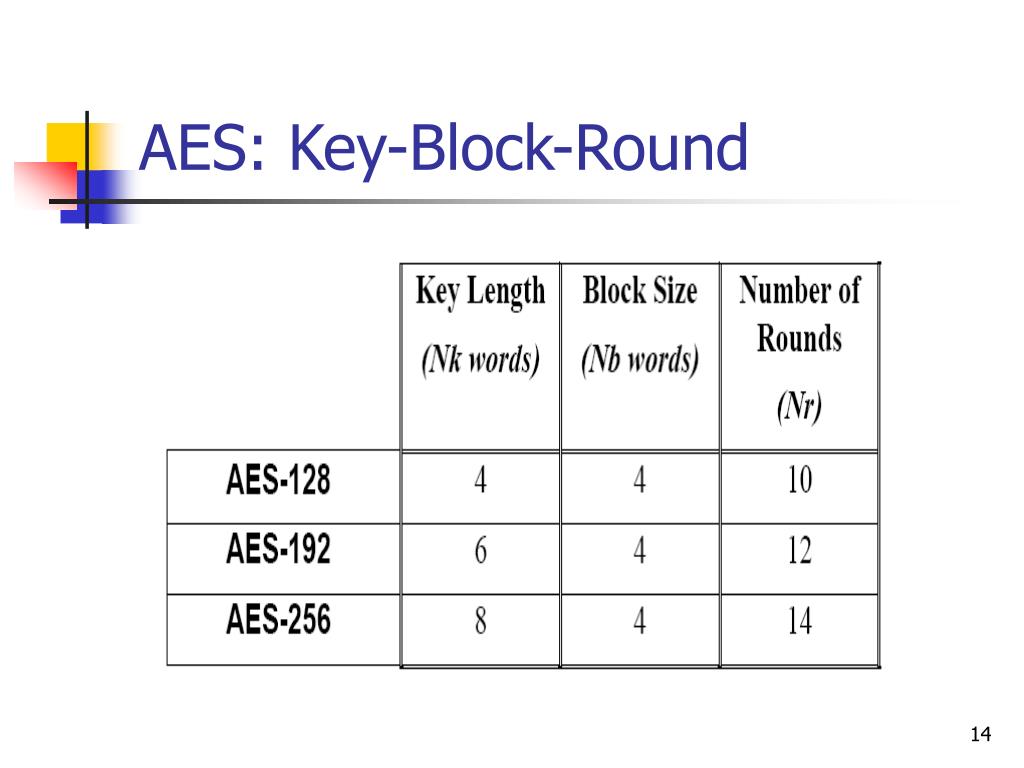
Introduction to AES (Advanced Encryption Standard)
►Introduction to DES Algorithm
What Is Block Cipher?
DES (Data Encryption Standard) Cipher Algorithm
►DES Key Schedule (Round Keys Generation) Algorithm
DES Decryption Algorithm
DES Algorithm - Illustrated with Java Programs
DES Algorithm Java Implementation
DES Algorithm - Java Implementation in JDK JCE
DES Encryption Operation Modes
DES in Stream Cipher Modes
PHP Implementation of DES - mcrypt
GTA V Keygen it's tool which generates a unique cd key/code for the game GTA V. This tool enables you to activate GTA V and play the game for free! Gta v cd key generator.
Blowfish - 8-Byte Block Cipher
Secret Key Generation and Management
Cipher - Secret Key Encryption and Decryption
Introduction of RSA Algorithm
RSA Implementation using java.math.BigInteger Class
Introduction of DSA (Digital Signature Algorithm)
Java Default Implementation of DSA
Private key and Public Key Pair Generation
PKCS#8/X.509 Private/Public Encoding Standards
Cipher - Public Key Encryption and Decryption
MD5 Mesasge Digest Algorithm
SHA1 Mesasge Digest Algorithm
OpenSSL Introduction and Installation
OpenSSL Generating and Managing RSA Keys
OpenSSL Managing Certificates
OpenSSL Generating and Signing CSR

OpenSSL Validating Certificate Path
'keytool' and 'keystore' from JDK
'OpenSSL' Signing CSR Generated by 'keytool'
Migrating Keys from 'keystore' to 'OpenSSL' Key Files
Certificate X.509 Standard and DER/PEM Formats
Migrating Keys from 'OpenSSL' Key Files to 'keystore'
Using Certificates in IE
Using Certificates in Google Chrome
Using Certificates in Firefox
Outdated Tutorials
References
Full Version in PDF/EPUB