Openssl Commands To Generate Private Key Without Passphrase
Deciding on Key Generation Options
- Openssl Genrsa Passphrase Argument
- Openssl Commands To Generate Private Key Without Passphrase Password
- Public Private Key Encryption
I'm using openssl to sign files, it works but I would like the private key file is encrypted with a password. These are the commands I'm using, I would like to know the equivalent commands using a. While Encrypting a File with a Password from the Command Line using OpenSSL is very useful in its own right, the real power of the OpenSSL library is its ability to support the use of public key cryptograph for encrypting or validating data in an unattended manner (where the password is not required to encrypt) is done with public keys. Jan 18, 2016 Generate a 2048 bit length private key without passphrase. Generate a 2048 bit length private key without passphrase. Skip navigation. Generate Private Key with OpenSSL Csaba Kerekes.
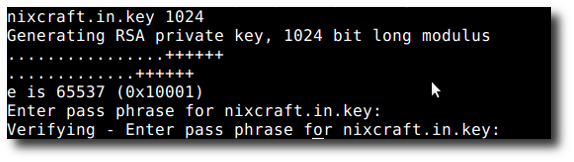
When generating a key, you have to decide three things: the key algorithm, the key size, and whether to use a passphrase.
Key Algorithm
For the key algorithm, you need to take into account its compatibility. For this reason, we recommend you use RSA. However, if you have a specific need to use another algorithm (such as ECDSA), you can use that too, but be aware of the compatibility issues you might run into.
Note: This guide only covers generating keys using the RSA algorithm.
Key Size
For the key size, you need to select a bit length of at least 2048 when using RSA and 256 when using ECDSA; these are the smallest key sizes allowed for SSL certificates. Unless you need to use a larger key size, we recommend sticking with 2048 with RSA and 256 with ECDSA.
Note: In older versions of OpenSSL, if no key size is specified, the default key size of 512 is used. Any key size lower than 2048 is considered unsecure and should never be used.
Passphrase
For the passphrase, you need to decide whether you want to use one. If used, the private key will be encrypted using the specified encryption method, and it will be impossible to use without the passphrase. Because there are pros and cons with both options, it's important you understand the implications of using or not using a passphrase. In this guide, we will not be using a passphrase in our examples.
One of the most versatile SSL tools is OpenSSL which is an open source implementation of the SSL protocol. There are versions of OpenSSL for nearly every platform, including Windows, Linux, and Mac OS X. OpenSSL is commonly used to create the CSR and private key for many different platforms, including Apache. However, it also has hundreds of different functions that allow you to view the details of a CSR or certificate, compare an MD5 hash of the certificate and private key (to make sure they match), verify that a certificate is installed properly on any website, and convert the certificate to a different format. A compiled version of OpenSSL for Windows can be found here.
If you don't want to bother with OpenSSL, you can do many of the same things with our SSL Certificate Tools. Below, we have listed the most common OpenSSL commands and their usage:
General OpenSSL Commands
These commands allow you to generate CSRs, Certificates, Private Keys and do other miscellaneous tasks.
- Generate a new private key and Certificate Signing Request
- Generate a self-signed certificate (see How to Create and Install an Apache Self Signed Certificate for more info)
- Generate a certificate signing request (CSR) for an existing private key
- Generate a certificate signing request based on an existing certificate
- Remove a passphrase from a private key
Checking Using OpenSSL
If you need to check the information within a Certificate, CSR or Private Key, use these commands. You can also check CSRs and check certificates using our online tools.
- Check a Certificate Signing Request (CSR)
- Check a private key
- Check a certificate
- Check a PKCS#12 file (.pfx or .p12)
Debugging Using OpenSSL
If you are receiving an error that the private doesn't match the certificate or that a certificate that you installed to a site is not trusted, try one of these commands. If you are trying to verify that an SSL certificate is installed correctly, be sure to check out the SSL Checker.
- Check an MD5 hash of the public key to ensure that it matches with what is in a CSR or private key
- Check an SSL connection. All the certificates (including Intermediates) should be displayed
Converting Using OpenSSL
Openssl Genrsa Passphrase Argument
Delta's key to the next generation toefl test pdf. These commands allow you to convert certificates and keys to different formats to make them compatible with specific types of servers or software. For example, you can convert a normal PEM file that would work with Apache to a PFX (PKCS#12) file and use it with Tomcat or IIS. Use our SSL Converter to convert certificates without messing with OpenSSL.
Openssl Commands To Generate Private Key Without Passphrase Password
- Convert a DER file (.crt .cer .der) to PEM
- Convert a PEM file to DER
- Convert a PKCS#12 file (.pfx .p12) containing a private key and certificates to PEM
You can add -nocerts to only output the private key or add -nokeys to only output the certificates.
- Convert a PEM certificate file and a private key to PKCS#12 (.pfx .p12)
Public Private Key Encryption
Originally posted on Sun Jan 13, 2008